![[Multi Cloud] AWS-OCI VPN Turnel 이중화(BGP)_2. AWS-OCI VPN1 구성 (AWS)](https://img1.daumcdn.net/thumb/R750x0/?scode=mtistory2&fname=https%3A%2F%2Fblog.kakaocdn.net%2Fdna%2FDcs6Z%2FdJMb81mtd7b%2FAAAAAAAAAAAAAAAAAAAAAD4CDdmOB7fQO2_Mgq-dXbzgsH1cuLghEQJi8efkcMUA%2Fimg.png%3Fcredential%3DyqXZFxpELC7KVnFOS48ylbz2pIh7yKj8%26expires%3D1772290799%26allow_ip%3D%26allow_referer%3D%26signature%3DCxZR%252FOvqB%252BGGDyzIVTQxCckJhkw%253D)

2.1. 임시 Customer Gateway
2.1.1. 개요
- OCI 측의 VPN Turnel IP를 Customer Gateway로 생성해야 하지만, 아직 OCI 측 Turnel IP를 모르기 때문에 임시 Customer Gateway를 생성 (1.1.1.1)
AWS vs OCI
Customer gateway는 OCI의 CPE에 해당하는 리소스
2.1.2. 설정
1. VPC → Customer Gateway → Create customer gateway 클릭

2. Create customer gateway
a. Name tag : <적절한 이름 입력>
b. BGP ASN : 31898 (OCI 측 ASN은 31898 사용)
c. IP address : <적절한 임시 IP 입력>

OCI 측 BGP ASN은 31898으로, 이를 변경할 수 있는 화면이 OCI Console 내 존재하지 않음 (변경 불가한 항목으로 보여짐, 공식적으로 불가하다라는 내용이 명시되어 있지는 않음)
(https://docs.oracle.com/en-us/iaas/Content/Network/Tasks/ip-sec-tunnel_update.htm)
3. 생성 확인

2.2. Transit gateway
2.2.1. 개요
- VPN 구성을 위해 Virtual private gateway도 가능하지만, 이는 단일 네트워크와의 연결을 위한 목적
- ex) 하나의 VCN - 하나의 On-premise/Cloud Network
AWS vs OCI
Transit gateway는 OCI의 DRG에 해당하는 리소스

2. Create transit gateway
a. Name tag : <적절한 이름 입력>
b. Description : <적절한 설명 입력>
c. Amazon side Autonomous System Number (ASN) : <AWS 측에서 이용할 ASN 번호 입력> (여기서는 입력하지 않고 기본 값으로 이용)

AWS에서 BGP 통신을 위한 ASN 번호의 기본 값은 64512이며,
Default or 64512-65535 or 4200000000-4294967294 중 선택하여 생성 가능
Amazon side Autonomous System Number(ASN) The Autonomous System Number (ASN) for the AWS side of a Border Gateway Protocol (BGP) session. You can use the default ASN, or you can specify a private ASN in the 64512-65534 or 4200000000-4294967294 ranges.
(https://docs.aws.amazon.com/vpc/latest/tgw/tgw-transit-gateways.html#create-tgw)
3. 생성 확인

2.2.2.2. VPC Attach
1. VPC → Transit gateway attachments → Create transit gateway attachment
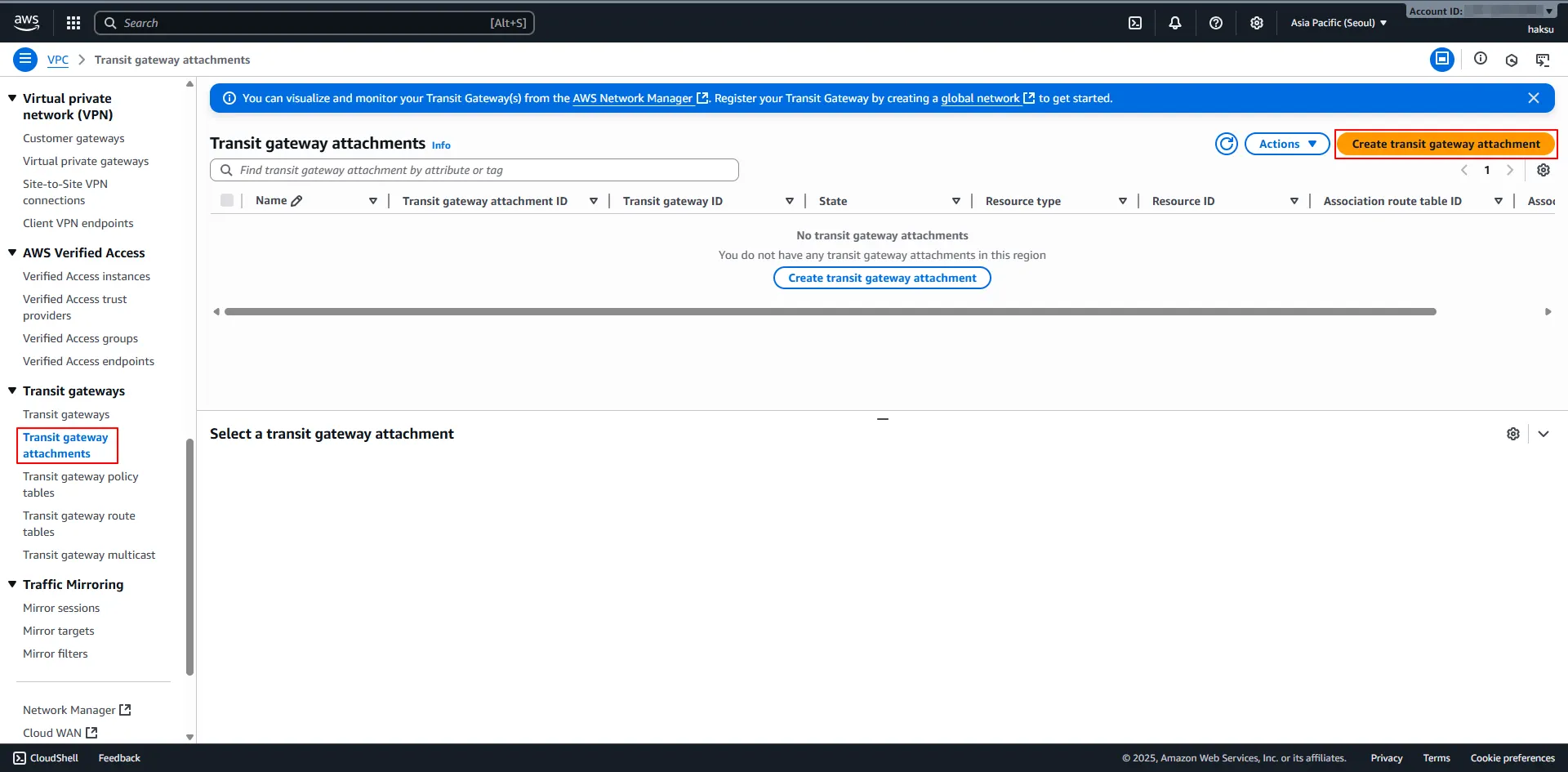
2. Create transit gateway attachment
a. Name tag : <적절한 이름 입력>
b. Transit gateway ID : <위에서 생성한 Transit gateway 선택>
c. Attachment type : VPC 선택
d. VPC ID : Attach 할 VPC 선택 및 Subnet 선택

3. 생성 확인

2.3. Site-to-Site VPN
2.3.1. VPN 생성
1. VPC → Virtual private network (VPN) Connections→ Create VPN Connection
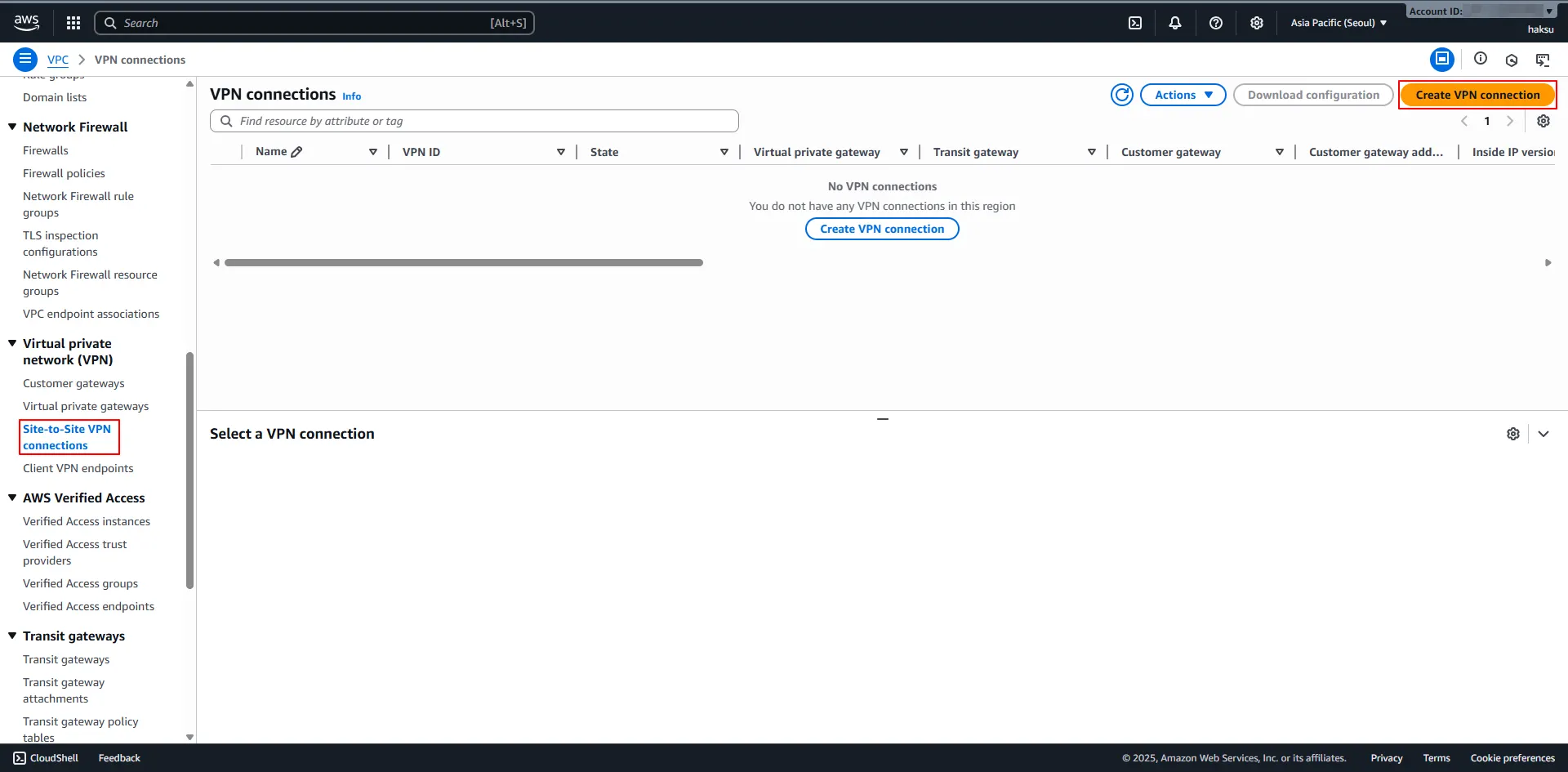
2. Create VPN connection
a. Name tag : <적절한 이름 입력>
b. Transit gateway type : Transit gateway 선택
c. Transit gateway : <위에서 생성한 Transit gateway 선택>
d. Customer gateway ID : <위에서 생성한 임시 Customer gateway 선택>
e. Routing options : Dynamic (requires BGP) 선택

3. Turnel 1 options - optional
a. Inside IPv4 CIDR for turnel 1 : <OCI 불가 CIDR 제외 하여 입력>
아래 IP 범위는 VPN Turnel Inside Interface로 사용 불가
169.254.10.0 ~ 169.254.19.255 169.254.100.0 ~ 169.254.109.255 169.254.192.0 ~ 169.254.201.255
( https://docs.oracle.com/en-us/iaas/Content/Network/Tasks/settingupIPsec.htm )
IPSec VPN 터널을 구성할 때, 터널 내부에서 서로 통신할 수 있는 IP 주소가 필요
VPN 터널의 내부 IP는 외부 인터넷이나 다른 네트워크와 직접 연결되지 않음
/30 Subnet을 선택해야 하는 이유는 VPN 터널 내부에서 단 두 개의 IP만 필요
b. Advanced options for turnel 1 : Phase 1, 2에서 사용할 알고리즘 선택 (여기서는 기본 값으로 이용)

4. 생성 확인

2.2.2. Configuration 다운 및 확인
1. 우측 상단 → Download configuration 클릭

2. Download configuration
a. Vendor : Generic 선택
b. Platform : Generic 선택
c. Software : Vendor Agnostic
d. IKE version : ikev2 선택

3. configuration 확인 (Turnel 1)
Amazon Web Services
Virtual Private Cloud
VPN Connection Configuration
================================================================================
AWS utilizes unique identifiers to manipulate the configuration of
a VPN Connection. Each VPN Connection is assigned a VPN Connection Identifier
and is associated with two other identifiers, namely the
Customer Gateway Identifier and the Virtual Private Gateway Identifier.
Your VPN Connection ID : vpn-07855594c097e0b6e
Your Virtual Private Gateway ID :
Your Customer Gateway ID : cgw-079524c4e95be47a7
A VPN Connection consists of a pair of IPSec tunnel security associations (SAs).
It is important that both tunnel security associations be configured.
IPSec Tunnel #1
================================================================================
#1: Internet Key Exchange Configuration
Configure the IKE SA as follows:
Please note, these sample configurations are for the minimum requirement of AES128, SHA1, and DH Group 2.
Category "VPN" connections in the GovCloud region have a minimum requirement of AES128, SHA2, and DH Group 14.
You will need to modify these sample configuration files to take advantage of AES256, SHA256, or other DH groups like 2, 14-18, 22, 23, and 24.
NOTE: If you customized tunnel options when creating or modifying your VPN connection, you may need to modify these sample configurations to match the custom settings for your tunnels.
Higher parameters are only available for VPNs of category "VPN," and not for "VPN-Classic".
The address of the external interface for your customer gateway must be a static address.
Your customer gateway may reside behind a device performing network address translation (NAT).
To ensure that NAT traversal (NAT-T) can function, you must adjust your firewall !rules to unblock UDP port 4500.
If not behind NAT, and you are not using an Accelerated VPN, we recommend disabling NAT-T. If you are using an Accelerated VPN, make sure that NAT-T is enabled.
- IKE version : IKEv2
- Authentication Method : Pre-Shared Key
- Pre-Shared Key : _lJuVJ3paFyw9NF._j_avGyt972Rro9.
- Authentication Algorithm : sha1
- Encryption Algorithm : aes-128-cbc
- Lifetime : 28800 seconds
- Phase 1 Negotiation Mode : main
- Diffie-Hellman : Group 2
#2: IPSec Configuration
Configure the IPSec SA as follows:
Category "VPN" connections in the GovCloud region have a minimum requirement of AES128, SHA2, and DH Group 14.
Please note, you may use these additionally supported IPSec parameters for encryption like AES256 and other DH groups like 2, 5, 14-18, 22, 23, and 24.
NOTE: If you customized tunnel options when creating or modifying your VPN connection, you may need to modify these sample configurations to match the custom settings for your tunnels.
Higher parameters are only available for VPNs of category "VPN," and not for "VPN-Classic".
- Protocol : esp
- Authentication Algorithm : hmac-sha1-96
- Encryption Algorithm : aes-128-cbc
- Lifetime : 3600 seconds
- Mode : tunnel
- Perfect Forward Secrecy : Diffie-Hellman Group 2
IPSec Dead Peer Detection (DPD) will be enabled on the AWS Endpoint. We
recommend configuring DPD on your endpoint as follows:
- DPD Interval : 10
- DPD Retries : 3
IPSec ESP (Encapsulating Security Payload) inserts additional
headers to transmit packets. These headers require additional space,
which reduces the amount of space available to transmit application data.
To limit the impact of this behavior, we recommend the following
configuration on your Customer Gateway:
- TCP MSS Adjustment : 1379 bytes
- Clear Don't Fragment Bit : enabled
- Fragmentation : Before encryption
#3: Tunnel Interface Configuration
Your Customer Gateway must be configured with a tunnel interface that is
associated with the IPSec tunnel. All traffic transmitted to the tunnel
interface is encrypted and transmitted to the Virtual Private Gateway.
The Customer Gateway and Virtual Private Gateway each have two addresses that relate
to this IPSec tunnel. Each contains an outside address, upon which encrypted
traffic is exchanged. Each also contain an inside address associated with
the tunnel interface.
The Customer Gateway outside IP address was provided when the Customer Gateway
was created. Changing the IP address requires the creation of a new
Customer Gateway.
The Customer Gateway inside IP address should be configured on your tunnel
interface.
Outside IP Addresses:
- Customer Gateway : 1.1.1.1
- Virtual Private Gateway : 3.38.86.169
Inside IP Addresses
- Customer Gateway : 169.254.40.2/30
- Virtual Private Gateway : 169.254.40.1/30
Configure your tunnel to fragment at the optimal size:
- Tunnel interface MTU : 1436 bytes
#4: Border Gateway Protocol (BGP) Configuration:
The Border Gateway Protocol (BGPv4) is used within the tunnel, between the inside
IP addresses, to exchange routes from the VPC to your home network. Each
BGP router has an Autonomous System Number (ASN). Your ASN was provided
to AWS when the Customer Gateway was created.
BGP Configuration Options:
- Customer Gateway ASN : 31898
- Virtual Private Gateway ASN : 64512
- Neighbor IP Address : 169.254.40.1
- Neighbor Hold Time : 30
Configure BGP to announce routes to the Virtual Private Gateway. The gateway
will announce prefixes to your customer gateway based upon the prefix you
assigned to the VPC at creation time.
4. configuration 확인 (Turnel 2)
IPSec Tunnel #2
================================================================================
#1: Internet Key Exchange Configuration
Configure the IKE SA as follows:
Please note, these sample configurations are for the minimum requirement of AES128, SHA1, and DH Group 2.
Category "VPN" connections in the GovCloud region have a minimum requirement of AES128, SHA2, and DH Group 14.
You will need to modify these sample configuration files to take advantage of AES256, SHA256, or other DH groups like 2, 14-18, 22, 23, and 24.
NOTE: If you customized tunnel options when creating or modifying your VPN connection, you may need to modify these sample configurations to match the custom settings for your tunnels.
Higher parameters are only available for VPNs of category "VPN," and not for "VPN-Classic".
The address of the external interface for your customer gateway must be a static address.
Your customer gateway may reside behind a device performing network address translation (NAT).
To ensure that NAT traversal (NAT-T) can function, you must adjust your firewall !rules to unblock UDP port 4500.
If not behind NAT, and you are not using an Accelerated VPN, we recommend disabling NAT-T. If you are using an Accelerated VPN, make sure that NAT-T is enabled.
- IKE version : IKEv2
- Authentication Method : Pre-Shared Key
- Pre-Shared Key : DH.C9D2IfDyUUyVBYRR87mV2mMbzw_Ud
- Authentication Algorithm : sha1
- Encryption Algorithm : aes-128-cbc
- Lifetime : 28800 seconds
- Phase 1 Negotiation Mode : main
- Diffie-Hellman : Group 2
#2: IPSec Configuration
Configure the IPSec SA as follows:
Category "VPN" connections in the GovCloud region have a minimum requirement of AES128, SHA2, and DH Group 14.
Please note, you may use these additionally supported IPSec parameters for encryption like AES256 and other DH groups like 2, 5, 14-18, 22, 23, and 24.
NOTE: If you customized tunnel options when creating or modifying your VPN connection, you may need to modify these sample configurations to match the custom settings for your tunnels.
Higher parameters are only available for VPNs of category "VPN," and not for "VPN-Classic".
- Protocol : esp
- Authentication Algorithm : hmac-sha1-96
- Encryption Algorithm : aes-128-cbc
- Lifetime : 3600 seconds
- Mode : tunnel
- Perfect Forward Secrecy : Diffie-Hellman Group 2
IPSec Dead Peer Detection (DPD) will be enabled on the AWS Endpoint. We
recommend configuring DPD on your endpoint as follows:
- DPD Interval : 10
- DPD Retries : 3
IPSec ESP (Encapsulating Security Payload) inserts additional
headers to transmit packets. These headers require additional space,
which reduces the amount of space available to transmit application data.
To limit the impact of this behavior, we recommend the following
configuration on your Customer Gateway:
- TCP MSS Adjustment : 1379 bytes
- Clear Don't Fragment Bit : enabled
- Fragmentation : Before encryption
#3: Tunnel Interface Configuration
Your Customer Gateway must be configured with a tunnel interface that is
associated with the IPSec tunnel. All traffic transmitted to the tunnel
interface is encrypted and transmitted to the Virtual Private Gateway.
The Customer Gateway and Virtual Private Gateway each have two addresses that relate
to this IPSec tunnel. Each contains an outside address, upon which encrypted
traffic is exchanged. Each also contain an inside address associated with
the tunnel interface.
The Customer Gateway outside IP address was provided when the Customer Gateway
was created. Changing the IP address requires the creation of a new
Customer Gateway.
The Customer Gateway inside IP address should be configured on your tunnel
interface.
Outside IP Addresses:
- Customer Gateway : 1.1.1.1
- Virtual Private Gateway : 52.79.161.27
Inside IP Addresses
- Customer Gateway : 169.254.149.226/30
- Virtual Private Gateway : 169.254.149.225/30
Configure your tunnel to fragment at the optimal size:
- Tunnel interface MTU : 1436 bytes
#4: Border Gateway Protocol (BGP) Configuration:
The Border Gateway Protocol (BGPv4) is used within the tunnel, between the inside
IP addresses, to exchange routes from the VPC to your home network. Each
BGP router has an Autonomous System Number (ASN). Your ASN was provided
to AWS when the Customer Gateway was created.
BGP Configuration Options:
- Customer Gateway ASN : 31898
- Virtual Private Gateway ASN : 64512
- Neighbor IP Address : 169.254.149.225
- Neighbor Hold Time : 30
Configure BGP to announce routes to the Virtual Private Gateway. The gateway
will announce prefixes to your customer gateway based upon the prefix you
assigned to the VPC at creation time.
Additional Notes and Questions
================================================================================
- Amazon Virtual Private Cloud Getting Started Guide:
http://docs.amazonwebservices.com/AmazonVPC/latest/GettingStartedGuide
- Amazon Virtual Private Cloud Network Administrator Guide:
http://docs.amazonwebservices.com/AmazonVPC/latest/NetworkAdminGuide'Cloud > Multi Cloud' 카테고리의 다른 글
| [Multi Cloud] AWS-OCI VPN Turnel 이중화 (BGP)_6. AWS-OCI VPN2 구성 (AWS) (0) | 2025.10.25 |
|---|---|
| [Multi Cloud] AWS-OCI VPN Turnel 이중화 (BGP)_5. 결과 확인 (0) | 2025.10.25 |
| [Multi Cloud] AWS-OCI VPN Turnel 이중화 (BGP)_4. AWS-OCI VPN1 구성 (AWS) (0) | 2025.10.25 |
| [Multi Cloud] AWS-OCI VPN Turnel 이중화 (BGP)_3. AWS-OCI VPN1 구성 (OCI) (0) | 2025.10.25 |
| [Multi Cloud] AWS-OCI VPN Turnel 이중화 (BGP)_1. 개요 (0) | 2025.10.25 |

개인 공부 목적으로 사용하는 블로그입니다 :)
포스팅이 좋았다면 "좋아요❤️" 또는 "구독👍🏻" 해주세요!
![[Multi Cloud] AWS-OCI VPN Turnel 이중화 (BGP)_5. 결과 확인](https://img1.daumcdn.net/thumb/R750x0/?scode=mtistory2&fname=https%3A%2F%2Fblog.kakaocdn.net%2Fdna%2FcB0kB9%2FdJMb9XdhDxg%2FAAAAAAAAAAAAAAAAAAAAAKBpKQUb6QQWut5n9AwQ5VI_FlIOqKYxA_AeeY4q61Jk%2Fimg.png%3Fcredential%3DyqXZFxpELC7KVnFOS48ylbz2pIh7yKj8%26expires%3D1772290799%26allow_ip%3D%26allow_referer%3D%26signature%3Du0%252FMCtYSETthhRdjbzrPAZDlJZQ%253D)
![[Multi Cloud] AWS-OCI VPN Turnel 이중화 (BGP)_4. AWS-OCI VPN1 구성 (AWS)](https://img1.daumcdn.net/thumb/R750x0/?scode=mtistory2&fname=https%3A%2F%2Fblog.kakaocdn.net%2Fdna%2Fn4vJQ%2FdJMb9P0IaUq%2FAAAAAAAAAAAAAAAAAAAAADI67KJOoSTHfRt795JjB9wNYMxyZ1--uVLwU8UoufSP%2Fimg.png%3Fcredential%3DyqXZFxpELC7KVnFOS48ylbz2pIh7yKj8%26expires%3D1772290799%26allow_ip%3D%26allow_referer%3D%26signature%3DUfgY4%252Bu53LPNes2gpaRJPiZdylU%253D)
![[Multi Cloud] AWS-OCI VPN Turnel 이중화 (BGP)_3. AWS-OCI VPN1 구성 (OCI)](https://img1.daumcdn.net/thumb/R750x0/?scode=mtistory2&fname=https%3A%2F%2Fblog.kakaocdn.net%2Fdna%2Fcvbnqu%2FdJMb9N9FdRI%2FAAAAAAAAAAAAAAAAAAAAAFOBJuSKqN7I6SbtfGSykytu8x6N7FPlia903jNlCevv%2Fimg.png%3Fcredential%3DyqXZFxpELC7KVnFOS48ylbz2pIh7yKj8%26expires%3D1772290799%26allow_ip%3D%26allow_referer%3D%26signature%3Dbt7IOAppeSiqxjYFEEQhag7lkxw%253D)